Jay Blanchard, LLC
Website & Web Application Development & Design
Secuity Fail: Passwords Limitations Are So 1996
April 2015
Admit it. As a developer we have done more to contribute to the failure of our customer's and user's online security because we are too stubborn or lazy to handle passwords properly. Just look at some of the fruit of our labor:
Password must be between 5 and 32 characters in length. Valid characters include letters, numbers, and underscore.
Password must be between 6 and 12 characters in length. Valid characters include letters and numbers.
Password must be a minimum of 8 characters and contain at least one capial letter, a number and a special character such as an underscore or exclamation point.
Then there is this gem. The original requirements were a minimum of 8 characters. Accidentally putting in 7 characters causes an error to appear before the user:
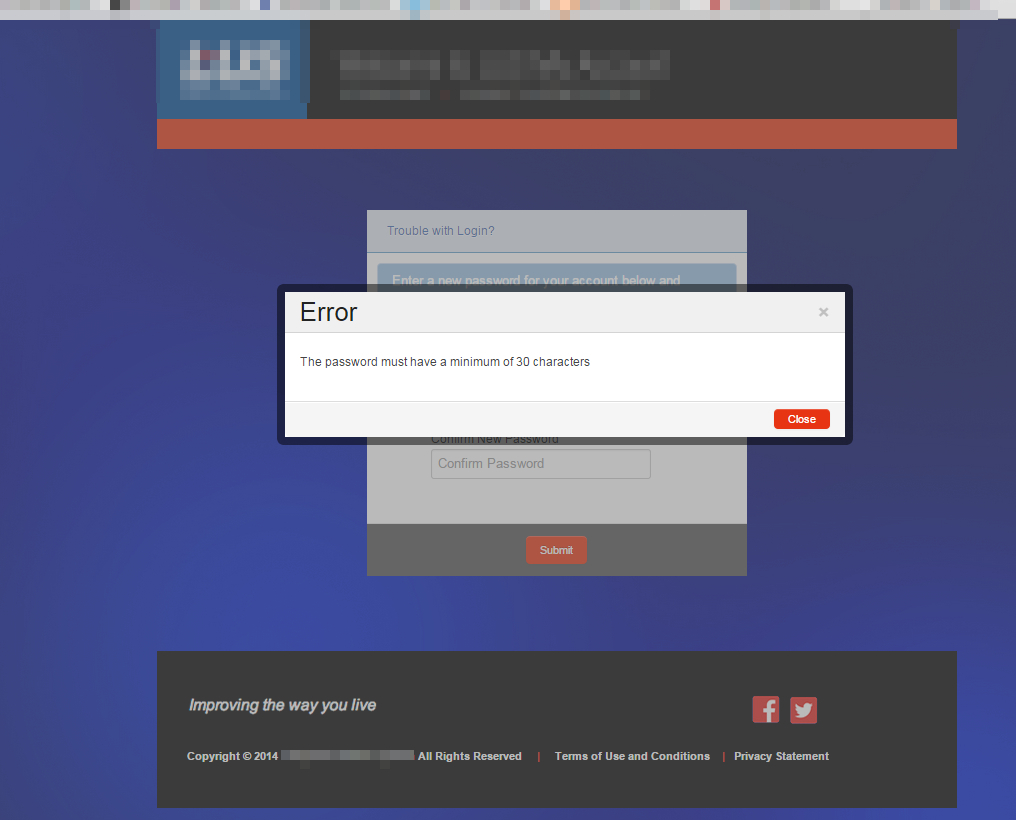
Note the tag line. Irony?
I could go on here, but I think you get the point. We have written code to support this nonsense, wrapping our heads around the right regex to account for every case. Agonizing over transmission, hashing and storage. We've talked about this so much the situation has even received proper pop culture status with its memorialization on xkcd.
There is no doubt our intentions were good. After all, users and customers cannot be expected to protect themselves properly. They don't create strong passwords, they use the word 'password' as their password more often than not. They don't heed the warnings, the news stories or the horror exrpressed by friends who have suffered through identity theft. The hacking of large retail chains phases them very little. We, as developers, set out to help our users avoid these pitfalls. I will alledge our attempts fell short and may have even contributed to the problem.
Very likely we've made it worse.
By placing arcane restrictions on passwords we have actually forced our users into a bad way of thinking and therefore made them seek the path of least resistance, simple, hackable passwords. We did this because we were used to restrictions on us. Sysadmins limited us to 8 characters so we projected the limit on to the rest of the world. It is time we stopped and learned how to handle any length of password with any character included. We may want to exclude white spaces from the password, but other than that we shouldn't place any restrictions on passwords.
Then we can encourage good security practices like passphrases or random words. Users, once they discover this, will be blissfully happy they don't have to remember some goofy combination of letters and numbers like f@rtp00p.
I can see you rolling your eyes. It means you have to learn how to properly hash passwords and how to compare entered passwords with the hashes. You'll have to toss some really hard won regex. Heaven forbid <ominous music insert here> you might have to refactor some code! Databases can hold very large hashed passwords and we should take advantage of the capability.
Keep in mind the general security of the data is on me, the developer along with the sysadmin and others. The security of a user's account in on them and I shouldn't do anything to hold them back. Personally I do not care what my users have for their passwords. All I do when users create their passwords is provide a strength meter and some basic guidelines:
"We have found using passphrases or multiple word combinations to be the most secure when it comes to preventing a hacker, who is trying to crack your login information, from being successful."
We need to remove the limitations on passwords and free up the users to own their security online. Are you in?
Comments? Shoot me your thoughts on Twiiter: @jaylblanchard